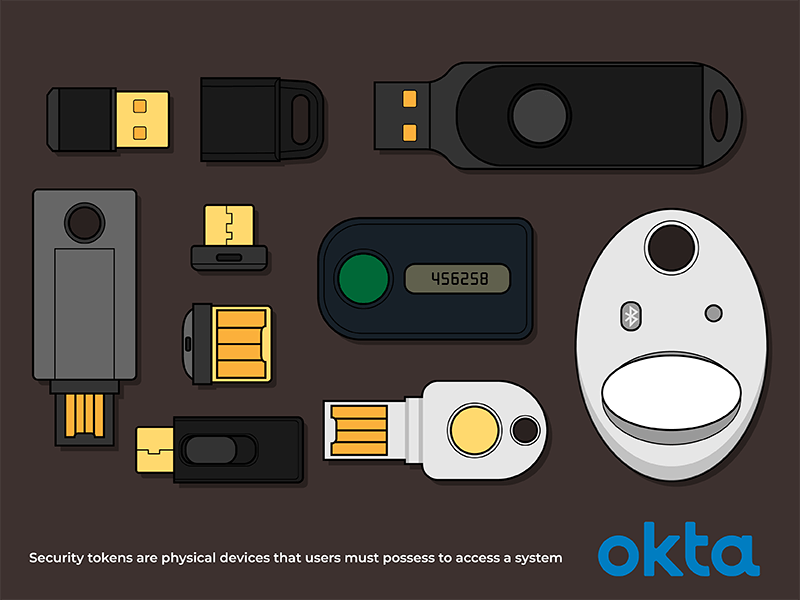
What Is a Security Token (or Authentication Token) and How Does It Work?
By A Mystery Man Writer
Last updated 08 Jul 2024
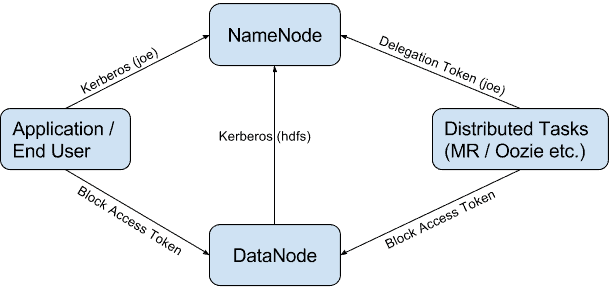
Hadoop Delegation Tokens Explained - Cloudera Blog

What Is Token-Based Authentication?
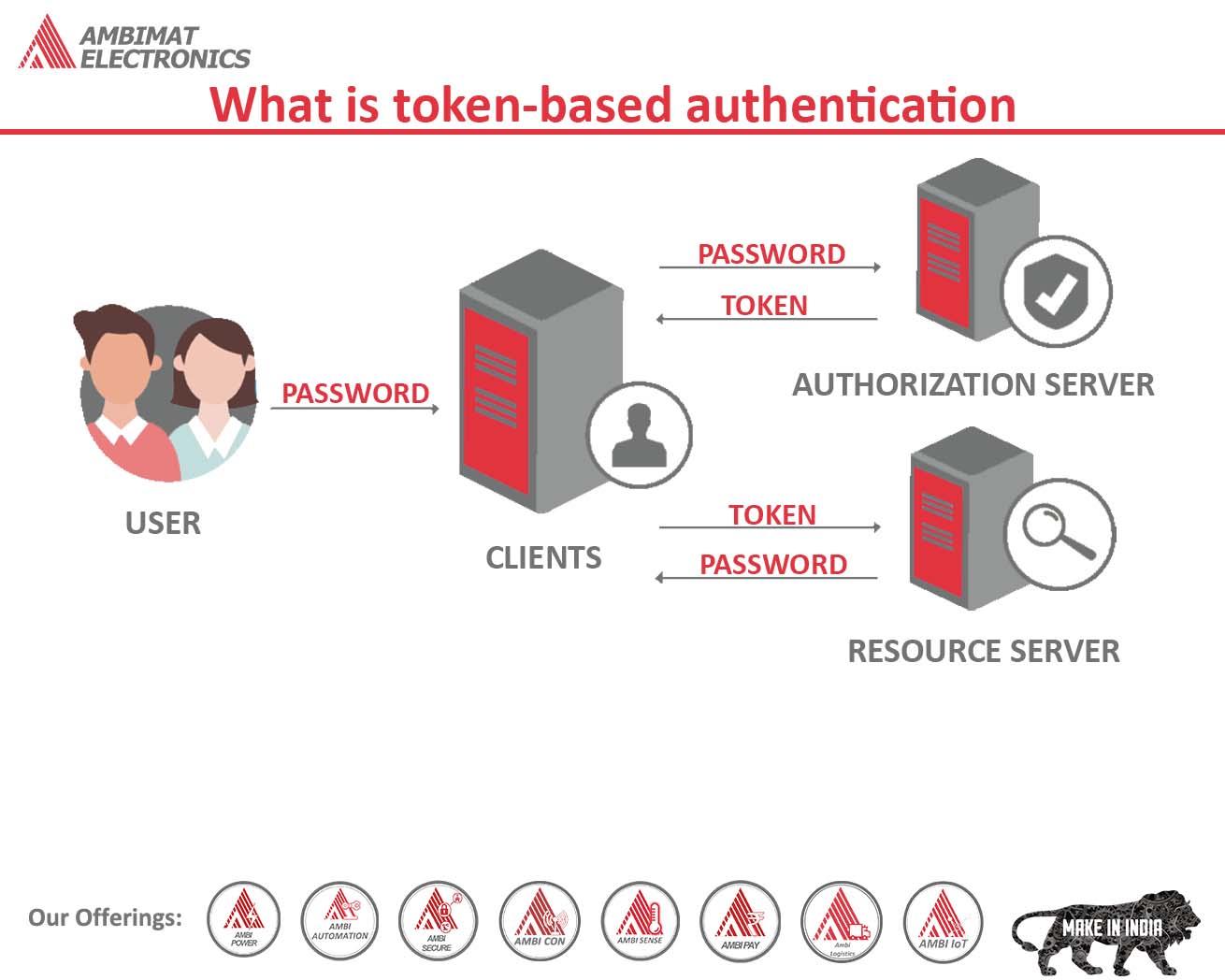
What is token-based authentication

STO 101: A beginner's guide on launching a security token offering

Token Sharing Approaches

Token tactics: How to prevent, detect, and respond to cloud token

Identity Providers: What is Token Based Authentication

What is an Authentication Token? A Detailed Review
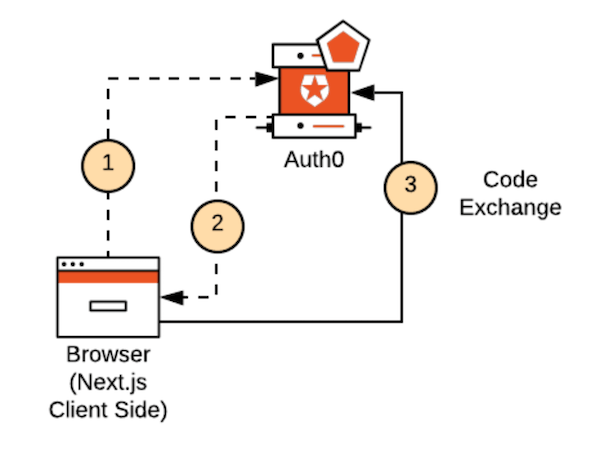
Token Storage
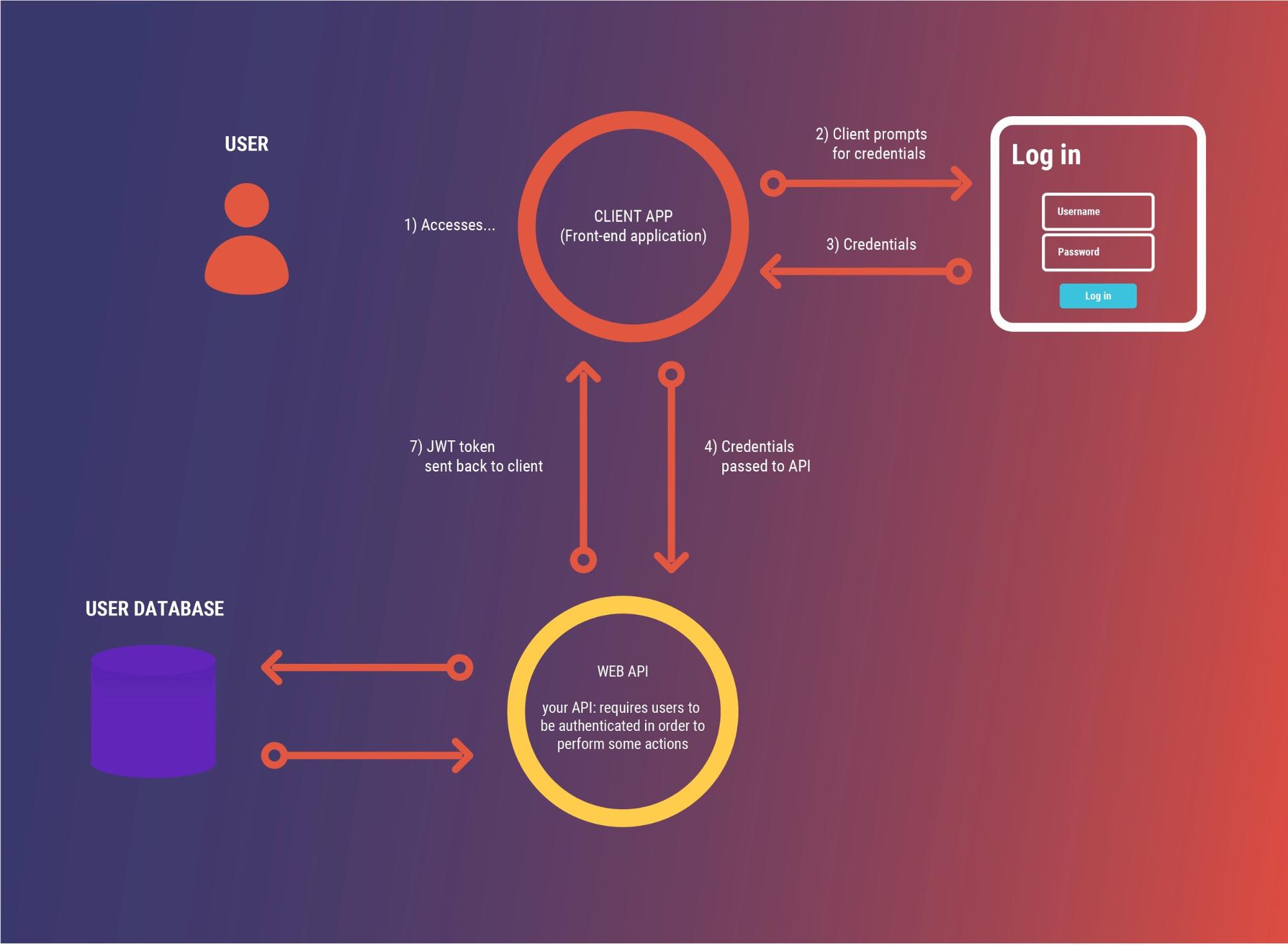
How JWT Helps in Securing Your API

Authentication Token: All You Need to Know

How JWT (JSON Web Token) authentication works? - DEV Community
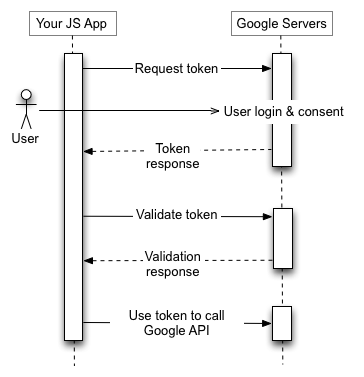
Using OAuth 2.0 to Access Google APIs, Authorization
Recommended for you
-
 What is a token?, Learn about crypto and DeFi08 Jul 2024
What is a token?, Learn about crypto and DeFi08 Jul 2024 -
 Personalised Tokens, Wooden Tokens08 Jul 2024
Personalised Tokens, Wooden Tokens08 Jul 2024 -
45,628+ Token Pictures Download Free Images on Unsplash08 Jul 2024
-
 Token2, Token2 c202 hardware token - 10 pack08 Jul 2024
Token2, Token2 c202 hardware token - 10 pack08 Jul 2024 -
 Chapter 13: Token Authentication, The Django Book08 Jul 2024
Chapter 13: Token Authentication, The Django Book08 Jul 2024 -
 Why you need a Bank Token and the Benefits08 Jul 2024
Why you need a Bank Token and the Benefits08 Jul 2024 -
 Hongkong Token08 Jul 2024
Hongkong Token08 Jul 2024 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/DDAI2L6BYJF6TAXGIK35LWWCEE.jpg) What Is DESK? FAQs about CoinDesk's Social Token08 Jul 2024
What Is DESK? FAQs about CoinDesk's Social Token08 Jul 2024 -
 What is an API token? 🔑 Quick Guide08 Jul 2024
What is an API token? 🔑 Quick Guide08 Jul 2024 -
 How to Validate an OpenID Connect ID Token08 Jul 2024
How to Validate an OpenID Connect ID Token08 Jul 2024
You may also like
-
 99.9% Soft Copper Wire 14 Gauge/ 1.63 mm Diameter 79 Feet / 24m 1 Pound Spool08 Jul 2024
99.9% Soft Copper Wire 14 Gauge/ 1.63 mm Diameter 79 Feet / 24m 1 Pound Spool08 Jul 2024 -
 Best Deal for Parima Travel Jewelry Case, Jewelry Boxes for Women Girls08 Jul 2024
Best Deal for Parima Travel Jewelry Case, Jewelry Boxes for Women Girls08 Jul 2024 -
Three Diamond Engagement Ring — Quercus Raleigh Custom08 Jul 2024
-
 Antique Borla / Mang Tikka /classic Design/indian Traditional Rajasthani Borla/ Rajasthani Tikka/ Borla /indian Jewelry08 Jul 2024
Antique Borla / Mang Tikka /classic Design/indian Traditional Rajasthani Borla/ Rajasthani Tikka/ Borla /indian Jewelry08 Jul 2024 -
 Gear Aid ReviveX Air Dry Water Repellent Spray - 5 fl oz can08 Jul 2024
Gear Aid ReviveX Air Dry Water Repellent Spray - 5 fl oz can08 Jul 2024 -
 DESIGNER PLUSH MOHAIR DARK SCARLET RED VELVET FURNITURE DRAPERY FABRIC BTY 55W08 Jul 2024
DESIGNER PLUSH MOHAIR DARK SCARLET RED VELVET FURNITURE DRAPERY FABRIC BTY 55W08 Jul 2024 -
 Fuchsia Pink Tulle Wedding Reception Decor - 6 x 100 Yards, Fabric Netting Ribbon, Valentine's Day, Easter, Wreath, Garland, Swag, Veil, Streamers08 Jul 2024
Fuchsia Pink Tulle Wedding Reception Decor - 6 x 100 Yards, Fabric Netting Ribbon, Valentine's Day, Easter, Wreath, Garland, Swag, Veil, Streamers08 Jul 2024 -
 Quick Car Coating Spray Car Polish Spray High Protection Car Shield Coating Waterless Car Wash Ceramic Spray Coating For Cars08 Jul 2024
Quick Car Coating Spray Car Polish Spray High Protection Car Shield Coating Waterless Car Wash Ceramic Spray Coating For Cars08 Jul 2024 -
 Painters Palette SVG File Print Art08 Jul 2024
Painters Palette SVG File Print Art08 Jul 2024 -
 Glitter Stars3 - Gold Black Star Sticker, Zazzle08 Jul 2024
Glitter Stars3 - Gold Black Star Sticker, Zazzle08 Jul 2024

