Four types of fake key attacks. Each diagram represents Alice
By A Mystery Man Writer
Last updated 16 May 2024
Download scientific diagram | Four types of fake key attacks. Each diagram represents Alice (left), her contacts (right), and an adversary (center). The green lines represent secure connections; the red lines represent compromised connections. Note that in each situation, there may be other pairs of clients communicating securely that are not shown. from publication: Automatic Detection of Fake Key Attacks in Secure Messaging | Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent | Automatism, Security and Server | ResearchGate, the professional network for scientists.
Digital signature - Wikipedia

Generic system model of physical layer security related to
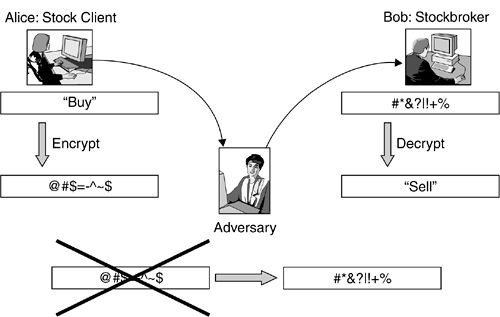
Public-Key Cryptography, The Theory of Cryptography

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging
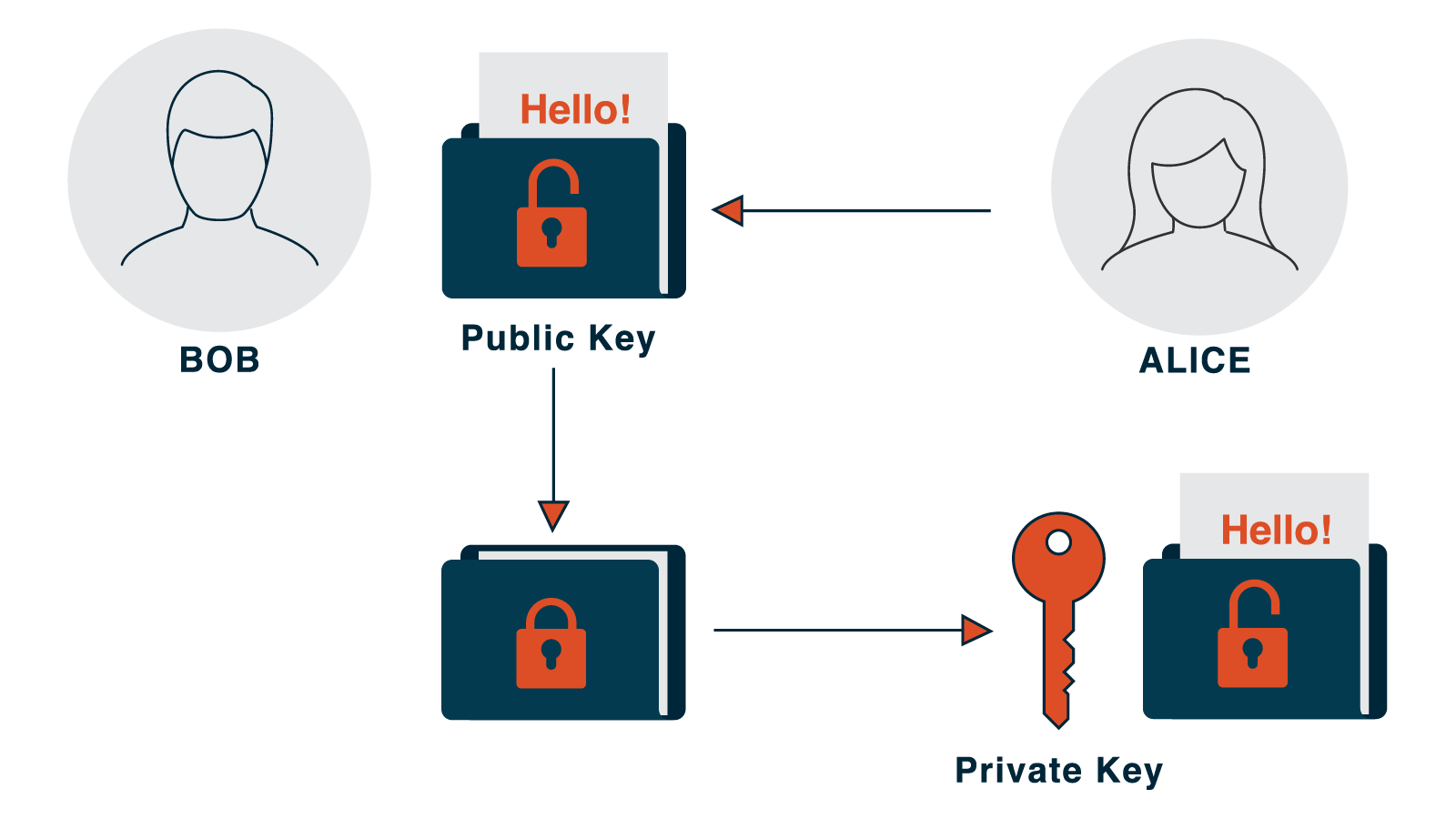
What is encryption? Our cyber experts decrypt the important facts
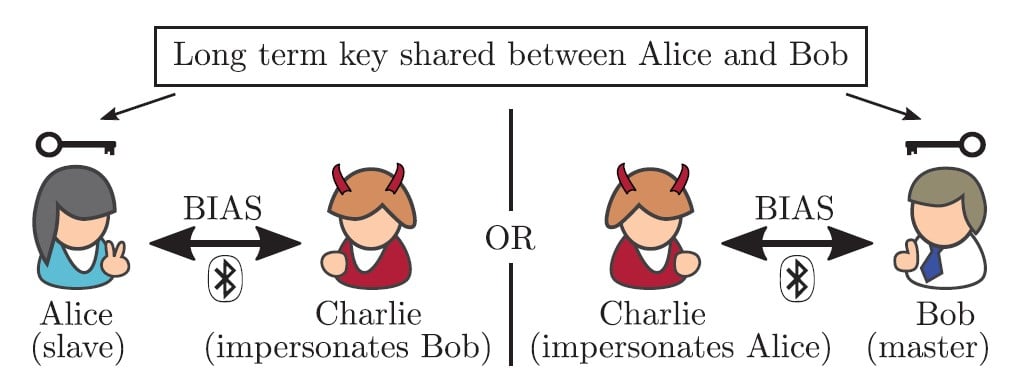
Introduction to Bluetooth attacks

10 Common Website Vulnerabilities: Security Tips

Active and Passive attacks in Information Security - GeeksforGeeks

Color online) Basic principles of faked-state attacks against BB84. As

Communication scenario of interest. Alice is the transmitter with Bob
Recommended for you
-
 Musical Smart Remote Key Toy Fake Car Toy Keys with Sound and Lights Fun and Educational Key Toys for Travel Play, Baby Toy, Baby Toy Smart Key Remote Car Control Musical Pretend16 May 2024
Musical Smart Remote Key Toy Fake Car Toy Keys with Sound and Lights Fun and Educational Key Toys for Travel Play, Baby Toy, Baby Toy Smart Key Remote Car Control Musical Pretend16 May 2024 -
 2391 Set of 6 fake keys16 May 2024
2391 Set of 6 fake keys16 May 2024 -
 You know those fake car keys that dealers would mail to try to get you to visit the dealership? My father kept some of them. I wonder …16 May 2024
You know those fake car keys that dealers would mail to try to get you to visit the dealership? My father kept some of them. I wonder …16 May 2024 -
 Streetwise™ Fake House Key Concealed Folding Knife - The Home Security Superstore16 May 2024
Streetwise™ Fake House Key Concealed Folding Knife - The Home Security Superstore16 May 2024 -
 » Blog Archive » Finding Another Utili-Key16 May 2024
» Blog Archive » Finding Another Utili-Key16 May 2024 -
Four types of fake key attacks. Each diagram represents Alice (left)16 May 2024
-
 Childish': Woman Backed for Fooling Unemployed Husband With Fake16 May 2024
Childish': Woman Backed for Fooling Unemployed Husband With Fake16 May 2024 -
 Hidden Storage Fake thermometer For Cash Cards Keys Diamond U Disk16 May 2024
Hidden Storage Fake thermometer For Cash Cards Keys Diamond U Disk16 May 2024 -
 Creative Dummy Car Key Case Mini Hidden Safe Box Secret16 May 2024
Creative Dummy Car Key Case Mini Hidden Safe Box Secret16 May 2024 -
) Buy Magicwand Multicolor Plastic and Metal Fake Car Remote Control16 May 2024
Buy Magicwand Multicolor Plastic and Metal Fake Car Remote Control16 May 2024
You may also like
-
![Plastic Welding Kit [Video] in 2023](https://i.pinimg.com/736x/35/a7/5c/35a75c9a5e7257d67c1bfb166c16bd09.jpg) Plastic Welding Kit [Video] in 202316 May 2024
Plastic Welding Kit [Video] in 202316 May 2024 -
 Mora Wood Carving Basic Knife16 May 2024
Mora Wood Carving Basic Knife16 May 2024 -
 Premium Levella PRF316300HS 3.1 Cubic Foot Manual Defrost Top16 May 2024
Premium Levella PRF316300HS 3.1 Cubic Foot Manual Defrost Top16 May 2024 -
 SHINY BLACK ICE 7mm 16 GA AWG Jump Rings / 5 Gram Pack (approx 70) / s – StravaMax Jewelry Etc16 May 2024
SHINY BLACK ICE 7mm 16 GA AWG Jump Rings / 5 Gram Pack (approx 70) / s – StravaMax Jewelry Etc16 May 2024 -
Natasha Kalimada on Instagram: Cozy 🧡 The best team ✨🪄✨✨ I16 May 2024
-
 Farmhouse Enamelware Rectangle Tray – Rustic Interiors LLC16 May 2024
Farmhouse Enamelware Rectangle Tray – Rustic Interiors LLC16 May 2024 -
 Apple Rind + Cinnamon - Highland Home Custom Creations16 May 2024
Apple Rind + Cinnamon - Highland Home Custom Creations16 May 2024 -
 VILLCASE 1 Set Dinosaur Painting Kits for Kids Ages 4-8 Sequins Painting Kits for Kids Ages 8-12 Diamond Art for Kids 5d Kit Animal with Box Art16 May 2024
VILLCASE 1 Set Dinosaur Painting Kits for Kids Ages 4-8 Sequins Painting Kits for Kids Ages 8-12 Diamond Art for Kids 5d Kit Animal with Box Art16 May 2024 -
 How to Hold a Guitar Pick & Best Guitar Picks16 May 2024
How to Hold a Guitar Pick & Best Guitar Picks16 May 2024 -
 Rolling Tray - Travis Scott - GrowLab16 May 2024
Rolling Tray - Travis Scott - GrowLab16 May 2024
